Hypertext Transfer Protocol Secure (HTTPS)

HTTPS
Hypertext Transfer Protocol Secure
HTTPS uses a combination of cryptographic protocols such as SSL (Secure Sockets Layer) or TLS (Transport Layer Security) to create a secure connection.
Port: 443 TCP | RFC:2818
OSI Layer: 7 (Application Layer)
Cyber Security Stance:
Designed by Vivekanand Padala
Protocol Overview
HTTPS is an extension of the standard HTTP protocol that adds a layer of encryption to protect sensitive information such as login credentials, credit card information, and other personal data from interception and unauthorized access.
To use HTTPS, a website needs an SSL/TLS certificate, which is issued by a trusted certificate authority. The certificate confirms that the website is authentic and that the connection is secure, which helps to build trust between the website and its visitors. Many websites use HTTPS by default, especially those that handle sensitive information or require users to log in.
Once the secure connection is established, all data transmitted between web browser and the web server is encrypted, making it difficult for hackers and other malicious actors to intercept and read the data. This helps to protect your sensitive information from theft and unauthorized access.
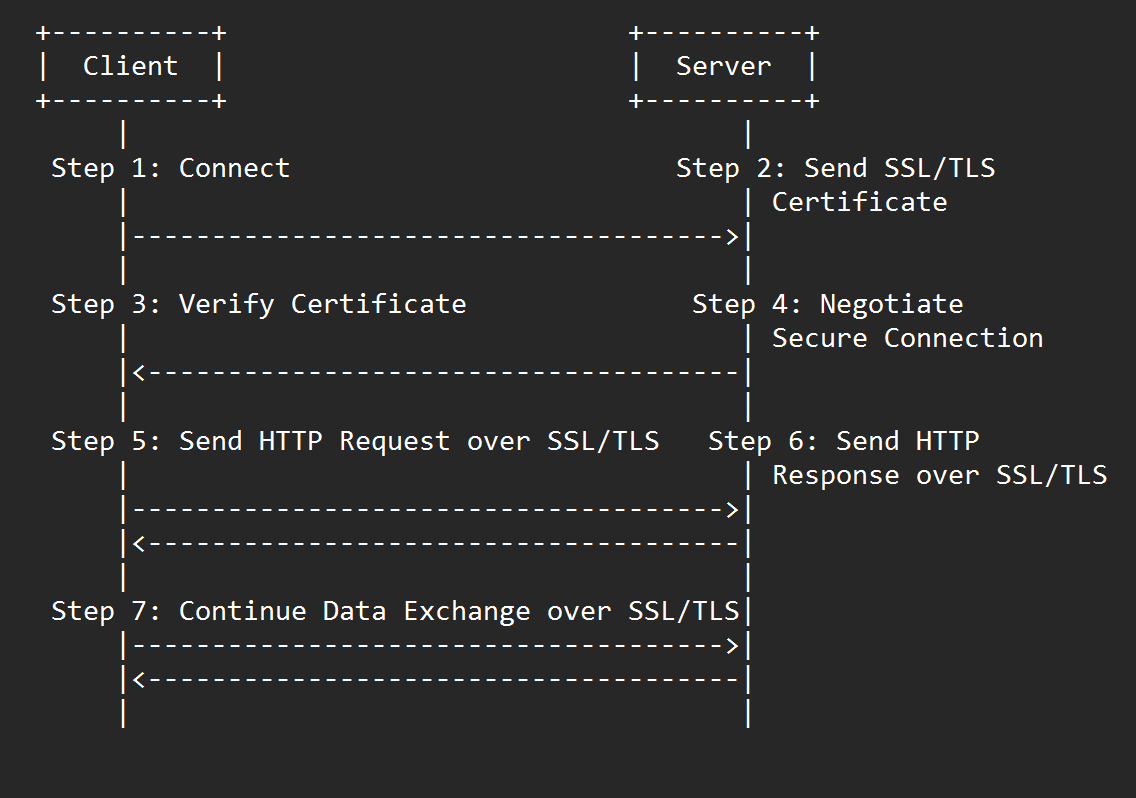
HTTPS workflow
- Client initiates a connection to the server. Typically a web browser, initiates a connection to the server by sending a request for a specific web page or resource.
- Server responds with its SSL/TLS certificate. The server responds to the client's request by sending its SSL/TLS certificate, which contains its public key and information about the certificate's issuer.
- Client verifies the certificate. The client verifies the SSL/TLS certificate to ensure that it is authentic and has been issued by a trusted certificate authority. This involves checking that the certificate's digital signature is valid and that the certificate has not expired or been revoked.
- Client and server negotiate a secure connection. Once the client has verified the server's SSL/TLS certificate, the client and server negotiate a secure connection using SSL/TLS. This involves the client and server agreeing on a set of cryptographic algorithms and exchanging cryptographic keys to encrypt and decrypt data transmitted between them.
- Client sends HTTP request over the secure connection. With the secure connection established, the client sends an HTTP request for the requested resource over the encrypted connection.
- Server sends HTTP response over the secure connection. The server responds to the client's request by sending an HTTP response over the secure connection, which is encrypted to protect the data from interception and unauthorized access.
- Client and server continue to exchange data over the secure connection Once the initial request and response have been sent, the client and server can continue to exchange data over the secure connection as needed, such as when the client requests additional resources or submits form data.