Secure Shell (SSH)

SSH
Secure Shell
SSH is a cryptographic network protocol used to securely connect to a remote computer or server over an unsecured network.
Port: 22 TCP | RFC:4251
OSI Layer: 7 (Application Layer)
Cyber Security Stance:
Designed by Vivekanand Padala
Protocol Overview
SSH, or Secure Shell, is a protocol used to securely connect to a remote computer or server over an unsecured network, such as the internet. The protocol provides strong encryption and authentication mechanisms to ensure that the communication between the client and server is secure and private.
The SSH protocol consists of several layers, each responsible for a specific aspect of the communication between the client and server.
- Transport Layer. It provides encryption, authentication, and integrity checks to ensure that the data is protected from eavesdropping, tampering, and forgery.
- User Authentication Layer. It provides various authentication methods, such as passwords, public key authentication, and multi-factor authentication.
- Connection Layer. It provides mechanisms for opening and closing the connection, as well as for multiplexing multiple logical channels over a single physical connection.
- Application Layer. It uses the lower layers to provide secure and reliable communication between the client and server.
The SSH protocol also defines various message formats, data types, and algorithms used in the protocol.
- Key Exchange Algorithm used to establish a shared secret key between the client and server, which is used to encrypt and decrypt the communication.
- Symmetric Encryption Algorithm used to encrypt and decrypt the data transmitted between the client and server.
- Message Authentication Code Algorithm used to ensure the integrity of the data transmitted between the client and server.
- Public Key Authentication Algorithm used to authenticate the client to the server using public key cryptography.
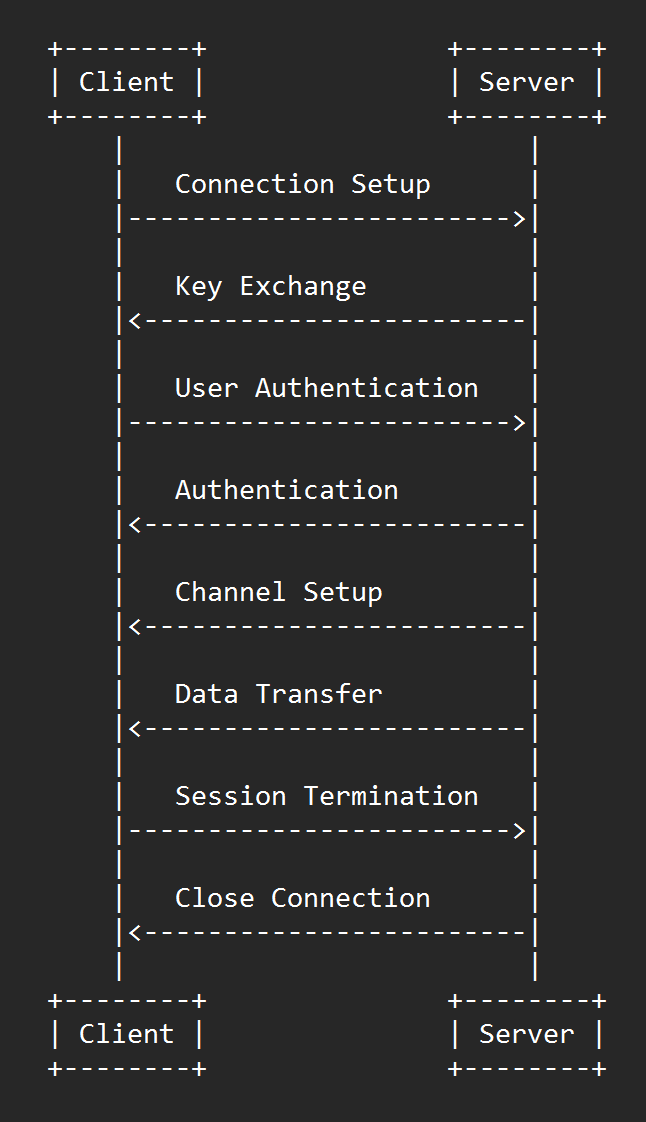
SSH workflow
- Connection Setup. The client initiates a connection to the SSH server.
- Key Exchange. The client and server perform a key exchange to establish a shared secret key. This key will be used for symmetric encryption of all communication between the client and server.
- User Authentication. The client provides authentication credentials to the server.
- Channel Setup. Once the client is authenticated, the client and server set up channels for communication. These channels are used for different purposes, such as interactive shell sessions, file transfers, or port forwarding.
- Data Transfer. The client and server use the established channels to transfer data between them.
- Session Termination. When the client is finished, it sends a termination signal to the server, and the server closes the SSH session.