Telnet

TELNET
TELetype NETwork
The Telnet protocol works by transmitting keystrokes and display information between the client and server over the network.
Port: 23 TCP | RFC:854
OSI Layer: 7 (Application Layer)
Cyber Security Stance:
Designed by Vivekanand Padala
Protocol Overview
Telnet is a protocol used for establishing a remote terminal session on a computer or other network device. It allows a user to connect to a remote host and interact with it as if they were sitting in front of the machine.
Telnet was developed in 1969 by a team of computer scientists at the Massachusetts Institute of Technology (MIT) led by John Melvin. The team created the Telnet protocol as a way to enable remote access to time-sharing computer systems, which were becoming increasingly common at the time.
The protocol does not encrypt data or provide any authentication or integrity guarantees, which makes it vulnerable to interception or modification by attackers. Nowadays, it has largely been replaced by more secure alternatives, such as SSH (Secure Shell). However, it is still used in some legacy systems or in situations where security is not a concern.
Some of the key features of the Telnet protocol include:
- Support for different terminal types and character sets
- Ability to transmit special control characters and escape sequences
- Support for user authentication and access control
- Ability to set terminal modes and options, such as echoing or line editing
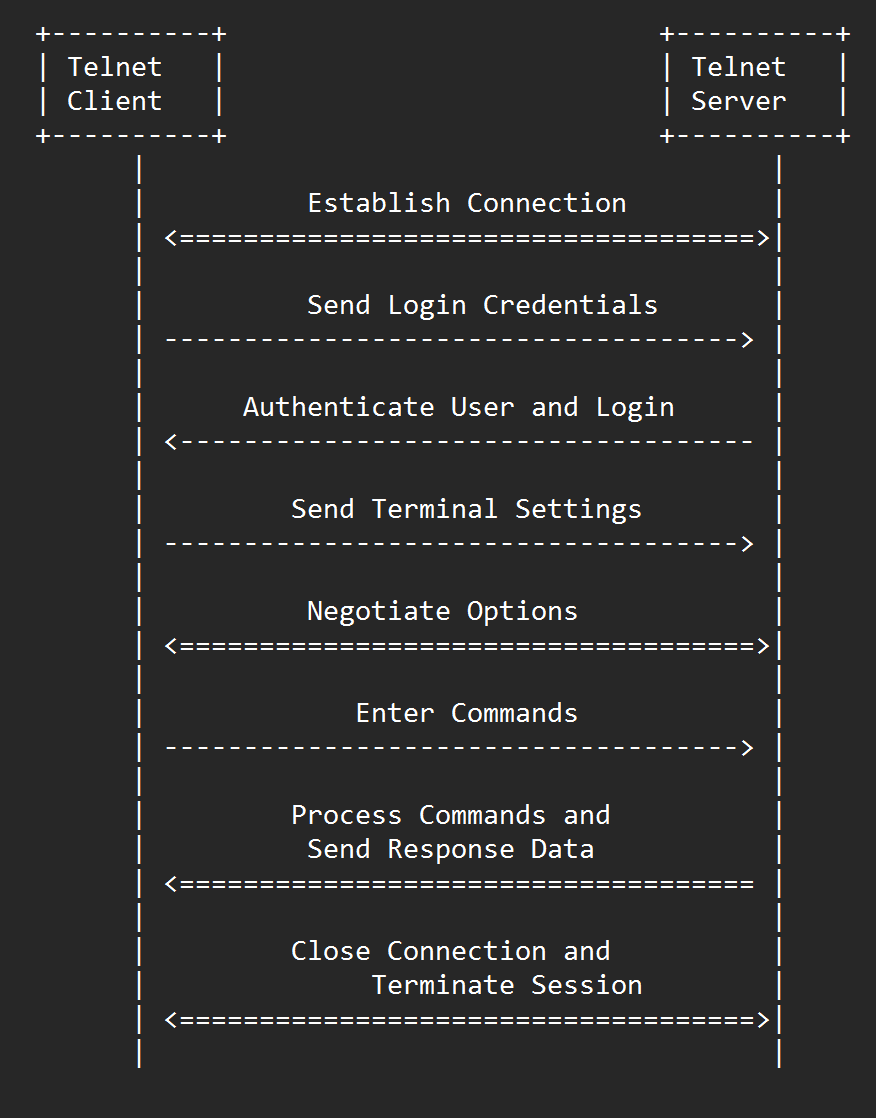
TELNET workflow
- Client initiates a connection to the Telnet server by specifying the hostname or IP address of the remote system and the port number of the Telnet service.
- The server responds with a welcome message that may include information about the system or the Telnet service.
- The client sends a series of commands and requests to the server, such as login credentials, terminal settings, and other options.
- The server responds with data and status messages, such as prompts, error messages, or output from executed commands.
- The client can interact with the remote system by sending keystrokes and special control characters, which are transmitted to the server over the Telnet connection.
- The server processes the incoming data and sends back response data or status messages, which are displayed on the client's terminal.
- The Telnet session continues until either the client or server terminates the connection, typically by sending a disconnect command or closing the connection.
Throughout the Telnet session, the client and server use a series of Telnet commands and responses to negotiate settings and control the behavior of the remote terminal session. These commands and responses are defined in the Telnet protocol specification, which includes a set of standard options and modes that can be used to customize the behavior of the Telnet session.